Authentication
All access-based security is unlocked by one (or more) of three things: what you have, what you know, or what you are. The what you have case is easy to explain and understand. The deadbolt on my front door needs a specific object — in this case a key — to open. Access to a website or your email might depend on a username plus password. That password is what you know. Access to a high-security vault might be protected by a fingerprint or retina scanner. That’s what you are. Unless you are part of Mission Impossible (or, ahem, have access to a gummy bear) you cannot have, know, and use someone else’s fingerprint.
I can loan my key to a buddy, but once he returns it (setting aside the whole key copying thing), he no longer has access to my house. If I give out the combination to the office supply room’s lock, though, that is just information and “information wants to be free.” I can tell someone, who tells three more people, who tells three more people, and suddenly there are no more post-it notes or pens. Or if I am not careful, someone can look over my shoulder as I type in the door code, getting access that way. You can’t “look over somebody’s shoulder” for a copy of the key (at least, you couldn’t until recently or even more recently). That’s the shortcoming with passwords. They are susceptible to being captured and once they’re known, they’re known.
Online systems that need a little extra security will sometimes use a combination of what you know + what you have instead of the baseline standard what you know (i.e. your password). For instance, my bank requires not just a login, but needs a special cookie in my browser. If I try to log in from a new computer, their system telephones me with an extra access code for confirmation. Now, in an effort to thwart spyware and phishing, Google offers similar 2-factor authentication.
Google’s 2-Factor Authentication
Google does 2-factor authentication through a combination of your login (what you know) and a smartphone app that generates a unique 6-digit number every minute that is specific to you (what you have). If you log in from a new web browser, you have to enter not only your username and password, but a recent number from the app. You only have to do this once per browser and/or once every 30 days. If you lose or break your smartphone, they give you a wallet-sized printout when you sign up of a dozen single-use passwords that you can use to log in. Using those, you can log in and turn off 2-factor authentication until you can otherwise resolve the situation. And you can always generate another wallet card at any time (though I think it voids the previous card).
Enabling It
If you are using a Google Apps account, your domain administrator will first have to enable 2-factor authentication on the domain. This does not automatically force it upon all users. Individual users still must opt in and go through the configuration steps. Enabling it for the domain simply gives users the option.
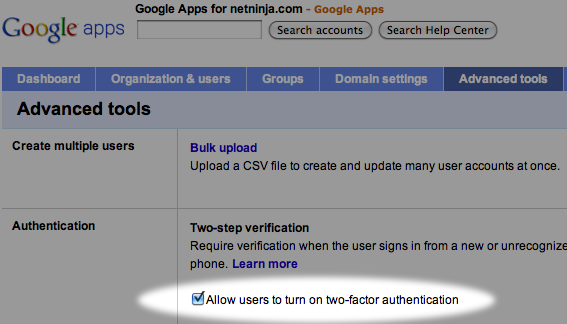
Next, you will need to go into your individual account settings and enable it for your account.
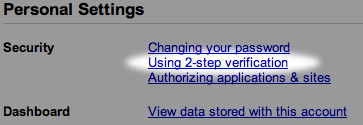
Enabling 2-factor will take you through a few steps. First, it will point you to the required smartphone app to install. You will install it as one of the steps in the process. In my case, it was Google Authenticator for the iPhone (iTunes Link). Once you have that installed, it needs to be configured to generate your unique set of PIN codes. With the iPhone, you take a photo of a barcode that Google’s website displays to you. This conveys a ton of information to the smartphone app. If your device does not have a camera (e.g. an iPod Touch), you get past this step by manually entering a bunch of information. Next, you are presented with a wallet card to print out and keep. This card has a bunch of single-use codes to log in. It is extra insurance in case your lose or break your smartphone.
Yes, it is a little weird that Google want you to have a few passwords WRITTEN DOWN! That goes against everything you’ve been told about passwords, right? Don’t write them down on post-it notes and don’t hide those notes under your keyboard. On the other hand, there is a perfectly secure system that has been used for centuries for keeping bits of paper safe. Those bits of paper are green and have denominations printed on them such as $20. If you keep a couple of backup passwords in the same spot, they will likely be relatively safe and secure.
Using It
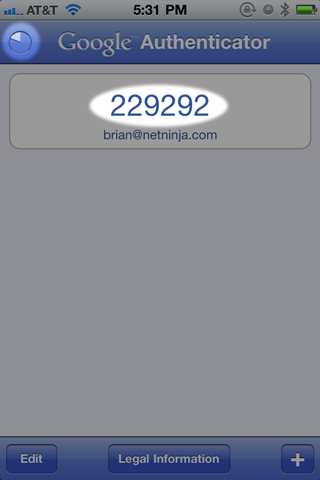
Using it is easy, you just launch the app and enter the current code.
The codes each last one minute, but if one is about to expire you can hold off until the next one comes around. The pie chart in the top-left corner counts down the time remaining on the current code and turns red when it is nearly done. If you do not have much time remaining, just wait until the next code appears.
Third-Party Apps
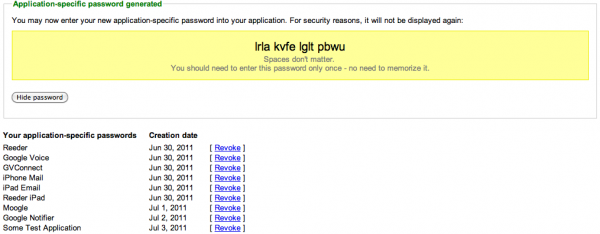
Not everything that connects to your Google account will understand two-factor authentication. An IMAP mail client (such as the default Mail.app on the iPhone) has no way to ask you for that extra PIN code. The same thing is true for a Google Reader client that wants to access your newsfeeds or Google Voice app that makes phone calls using your account. For these, you generate single-use (“nonce”) passwords. You can have Google generate one unique password per app. You see these passwords once, long enough to type into the app, then they are lost forever. The app can continue using the same password, but you have no way to retrieve it again. If you must reset an app and re-enter your authentication information, you will need to revoke the old password and generate a new one. The UI and process for doing this is extremely easy. Though the long passwords are secure, they are also sometimes a bit awkward to enter into the iPhone keyboard.
Summary
Overall, I am happy with the 2-factor authentication experience at Google. By design, such a process must be a little awkward — after all, you now have two password-like things to enter, one of which changes on its own — but their implementation makes it simple. You only have to type in the extra code if you’re at a new browser or if it has expired, and it doesn’t expire for 30 days. Setting up 3rd party apps is a one-time “set it and forget it” task that continues to work — you do not have to revisit it in 30 days.
If your Gmail is important to you and if you have the opportunity to enable 2-factor authentication, then I highly encourage you to do so.

My co-worker told me about two-step verification or “tinfoil hat mode” as he calls it a while ago and thus far my experience has been very positive. I will say that I use a LOT of apps that need my Google account – chat clients, mail clients, Chrome (sync) and the like on my phone, iPad, home computer and work computer – but as you described, the process isn’t too bad. I found copying and pasting on the mobile devices worked better than trying to type them in.
Anyway, great write up on it!
Very nice summary with useful images. Thanks for the informative article.